by Marisa Tassone and Ka Ki To
Post 1
Why should we be concerned about Internet Security

The Internet has made our lives so much more convenient as it allows us to shop online, bank online and share something on the social media with people all over the world! While we can enjoy all these aspects, we should also understand how to be safe online. Some people may think that things such as sending an email to a specific recipient will only be revealed to the designated person, however there are a lot more in between. These in-between steps are things we need to be concerned with.
A huge concern with online security is cookies. Cookies are used to tracking what you have done online and where you have been online. Another one is online privacy; the information that you post about your personal life are not just visible to your friends and families without the proper security measures. They can also be accessible by other people who you have never met. Cybercrime is also rampant in our interoperable world and requires our attention. We should deal with these with care.
Even though there are many things to be watched out for online, using the internet has become apart of our daily lives and we would not want to live in a world without it. Luckily there are some practices to follow for us to be protected from main security issues.
Post 2
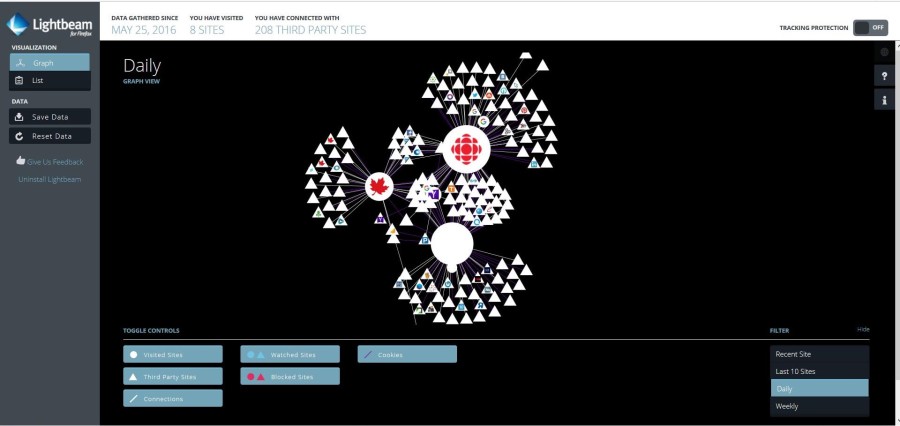
Cookies and internet security

Cookies are small bits of code that are embedded onto your computer while browsing websites on the internet; they are used to keep track of interactions on sites as well as specific interactions with third party sites. However, there are various types of cookies that can be embedded onto your computer.
The first type of cookie is the “tracking” cookie. These cookies are generally set on your computer by advertising companies to display ads that are specifically tailed to your perceived interests based on the movements they see you make along the internet. The data collected can be used by both first parties and third parties.
The second type of cookie is the “authentification” cookie which are generally used by first parties. These help identify you as a unique visitor to a site and record your interactions on said site. These cookies make much of the simplicity of the internet possible. For example, authentification cookies allow automatic log-ins as well as permit online shopping – both of which would not be possible if the cookie could not track you from one page to another.
Third party data is stored by “Data Brokers” that have specific profiles outlining information about sites you visit, online purchases you make, and even articles you have read. This profile also contains your Laptops IP address and cell phone GPS locations. Based on this, the data brokers can split us into very specific demographics based on various factors. This allows advertisers to specifically target ads to the right people. Not only does it allow the advertisers to target specific age groups but also interest groups as well, hugely broadening the scope of who they can target.
From this information, it is simple to see the positives of cookie use however the ability for third parties to track a certain IP address and be able to see their sites and path is worrisome when you think about who could be watching every step you take on the internet.
Post 3
Ways to Reduce Risks of Going Online

On the last blogs posts, we have talked about concerns and risks of going online. While we have to live with them, there are things we can do to manage them better. The following are several ways we can deal with and minimize the risks.
- Change the setting of the browser to minimize the sharing of our information. Go to your browser settings where you can do limit the sharing of information.
- Blocking cookies and trackers to stop the tracking of your interactions online.
- Choosing another way such as email and chat to share information.
- Choosing a safer browser. Firefox and Google Chrome are generally safer browsers than others.
- Installing Antivirus software that has better protection from viruses.
- Paying attention to details such as suspicious email and those links in the email contents.
There are lot of way we can do to reduce risks. This article from Entrepreneur also provides good advices to reduce those risks. I think one key to this is to increase awareness about it. Learning more about how these risks affect our usage of the internet and ways to prevent them will make us enjoying the advantages more.
Post 4
Cybercrime

There are many types of cybercrime to be aware of when on the internet but of all the various ways cybercrimes can be committed, there are four main cybercrimes.
The most common kind of cybercrime is Malware which is when a program or website uploads unwanted and likely destructive code to your computer. The malware (malicious code) is able to have various implications on your computer. These implications can range from extensive criminal activity to a simple nuisance. The less malicious malware can be something as simple as adware on the computer prompting annoying pop-ups whenever you start various programs. In the present day this harmless malware is much less of an issue as many web browsers have increased security designed to stop adware from being downloaded. However, the more common forms of malware are much more dangerous than simple adware. Some forms of malware can access your computer remotely allowing the hacker to use your camera and Bluetooth and keep track of keystrokes. However, these harmful viruses cannot install themselves on your computer. You are required to click the install button; hackers purposely design the button as various things to trick you into clicking it without your awareness; generally, though phishing and spoofing. This has become a growing concern over time as a result of interoperability becoming so common.
Phishing is a kind of cybercrime in which hackers/phishers contact people using email, websites, or telephone calls/messages and ask directly for information like logins or passwords. Some even prompt people to click a link that installs malware directly onto the computer.
A sub-concept of phishing is called spoofing. Essentially, spoofing is a dummy website that is an impersonation of an existing website or organization. These spoof sites are used to have you log-in to a familiar site and then upon clicking a button you download the malware onto your computer. Similar to a counterfeit designer bag, there is something that is always slightly “off” about the design. Upon looking closer you could see that the site doesn’t look quite right, paying attention and recognizing these signs could save you from cybercrime.
Post 5
Being safe online

Being safe online is a combination of being vigilant and equipping yourself with the correct software to protect yourself from internet threats. The technological world moves very quickly and new developments are made daily by hackers – its very important to keep yourself as safe as you can on the internet.
Running an antivirus software is incredibly important to have on your computer. Regardless of the computer platform you’re using, it’s absolutely vital to have a good antivirus software running and scanning for various possible viruses. It also is helpful to run the same sort of antivirus software on your smartphone to protect and scan for viruses on your phone which could spread onto your computer using Bluetooth or other connecting services.
Having a good web browser is also a great place to start to protect yourself online as well. Internet Explorer tends to have less resistance to threats than browsers like Google Chrome and Mozilla Firefox. The lack of interoperability of Google Chrome and Mozilla Firefox tends to promote its safety as a piece of malware that gets into one device cannot spread as easily as it can on Explorer. Ensuring your browser is updated regularly is also highly important as these companies often release security updates to protect your computer further. Both Firefox and Chrome also have the ability to install free add-ons and security patches to make your browser even more safe.
Of course, being vigilant is one of the most valuable tools you can use in protecting yourself from viruses on the computer. Understanding that hackers are trying to trick you into downloading and installing malicious code – understand that many reputable organizations would not contact you via the internet/email; it one is trying to, it may be fraudulent.
Check out Norton by Symantec’s prevention tips to stay safe when surfing online!
SOURCES:
Image 1: https://commons.wikimedia.org/wiki/File:Credit_card_theft.jpg
Image 2: https://commons.wikimedia.org/wiki/File:Stoned-virus-hexacode.png
Image 3: https://pixabay.com/en/antivirus-vector-technology-1349649/
Image 4: Created by Marisa Tassone
Image 5: https://www.flickr.com/photos/111692634@N04/18495846450